HOTWO:Ubiquiti
HOWTO:Ubiquiti
Ubiquiti is a manufacturer of popular home and small-business routers and wireless solutions. Most of their solutions run their own proprietary "EdgeOS" although the interface should be familiar and is (I think) based on Linux.
Typical Router Configuration
Ubuquiti routers can be configured in many, many ways but this solution is designed primarily for typical small networks, with a small set of internal subnets and then a single outbound connection to the broader internet. The solution requires that you have configured and know the internal subnets and that those subnets won't change. There's no automatic routing here, this is all static configuration.
In the default mode, the internal networks are configured as NAT subnets and internal addresses are rewritten as they egress the router. When running CAIDA's Spoofer tool, you are told that real spoofing can't be tested, but that all addresses are rewritten. From what I can tell, this means that a malicious internal system will be able to successfully send packets to a remote DOS target, but that target will see that network traffic as coming from the external address of your home router. Probably not what you want.
Adding Egress Filtering
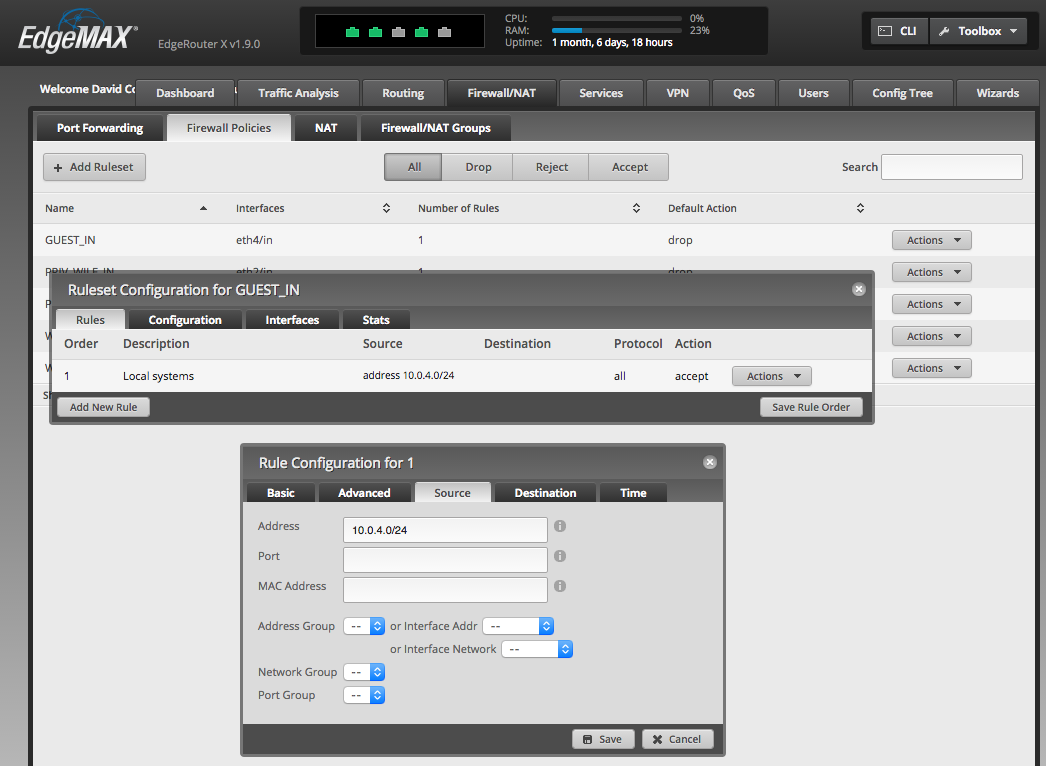
The solution here is fairly simple: add firewall rules to the internal interfaces to only accept traffic from the assigned subnet IPs. You can do this through the user interface: see the Firewall/NAT tab, then select Firewall Policies, then Add Rulesets as appropriate. I added a separate ruleset for each interface (three in my case), assigned the ruleset to the "IN" traffic for each interface, then created an "accept" rule for the known subnet traffic, and then set the default policy to "drop".
The resulting configuration snippet from the config file looks like this:
name GUEST_IN {
default-action drop
description "Guest wireless in"
rule 1 {
action accept
description "Local systems"
log disable
protocol all
source {
address 10.0.4.0/24
}
}
}